We have so far treated with the propagation factor across a classically
allowed region, finding that whether the particle is moving to the left
or the right, this factor is given by ![]() where a is the
length of the region and k is the constant wave vector across the
region. In general, we will also need a propagation factors for
forbidden regions. The zero-centered form for an acceptable wave
function for a forbidden region extending in the region x;SPMgt;0 is
where a is the
length of the region and k is the constant wave vector across the
region. In general, we will also need a propagation factors for
forbidden regions. The zero-centered form for an acceptable wave
function for a forbidden region extending in the region x;SPMgt;0 is
![]() where
where ![]() . A
corresponding wave function centered at the point x=a will be
. A
corresponding wave function centered at the point x=a will be
![]() . In the same way as we generated the
propagation factor for a classically allowed (9) region,
these two wave functions are related by the propagation factor for a
classically forbidden region, c(x)=p e(x) where
. In the same way as we generated the
propagation factor for a classically allowed (9) region,
these two wave functions are related by the propagation factor for a
classically forbidden region, c(x)=p e(x) where ![]() .
.
For classically forbidden regions the exponential solutions carry no
current and we must decide which of the two exponential solutions
![]() we regard as traveling to the right and which as
traveling left. We must also decide how to normalize the standard
unit solution.
Any choice of normalization is valid so long
as we are consistent in our assignment of quantum amplitudes.
However, we seek to make a choice in normalization which leads to
the most natural assignment of quantum amplitudes.
we regard as traveling to the right and which as
traveling left. We must also decide how to normalize the standard
unit solution.
Any choice of normalization is valid so long
as we are consistent in our assignment of quantum amplitudes.
However, we seek to make a choice in normalization which leads to
the most natural assignment of quantum amplitudes.
As we observed in the previous paragraph, when a left incident
particle collides with a forbidden region extending across the entire
region x;SPMgt;0, the only acceptable form for the solution for x;SPMgt; is
![]() , which therefore must play the role which the
transmitted wave
, which therefore must play the role which the
transmitted wave ![]() plays in the classically allowed case.
We thus identify
plays in the classically allowed case.
We thus identify ![]() as a solution ``penetrating to the
right'' and
as a solution ``penetrating to the
right'' and ![]() as a solution ``penetrating to the
left.'' We then use these forms as the sole component of the
solution in the transmitted region when scattering into a forbidden
region from the left or right.
as a solution ``penetrating to the
left.'' We then use these forms as the sole component of the
solution in the transmitted region when scattering into a forbidden
region from the left or right.
The mathematical way of expressing this identification is to use the
concept of analytic continuation, which, in loose terms, simply
means allowing a variable which we normally regard as real to take on
complex values. Consider for example the wave vector
![]() which insures that
the functions
which insures that
the functions ![]() satisfy the TISE for a potential
satisfy the TISE for a potential ![]() .
In
classically forbidden regions (
.
In
classically forbidden regions ( ![]() ) we generally
do not work with k because it becomes imaginary. However, there is
no mathematical reason preventing us from working with imaginary k.
The mathematics used in deriving our solutions to
the TISE works just as well for complex numbers as it does
for real numbers.
) we generally
do not work with k because it becomes imaginary. However, there is
no mathematical reason preventing us from working with imaginary k.
The mathematics used in deriving our solutions to
the TISE works just as well for complex numbers as it does
for real numbers.
An imaginary k simply means that the solutions
![]() are actually the
exponentially growing and shrinking solutions which we expect. In
fact,
are actually the
exponentially growing and shrinking solutions which we expect. In
fact,

so that ![]() , which is precisely
correct. Similarly, we may take any wave function,
which had been computed under the assumption that a given region is
classically allowed, and by substituting
, which is precisely
correct. Similarly, we may take any wave function,
which had been computed under the assumption that a given region is
classically allowed, and by substituting ![]() find a
valid solution for the classically forbidden case.
The only ambiguity which we must resolve is the choice of
sign for k. To resolve this, note that if we take a classically
allowed scattering solution, the wave function in the transmitted region
appears as
find a
valid solution for the classically forbidden case.
The only ambiguity which we must resolve is the choice of
sign for k. To resolve this, note that if we take a classically
allowed scattering solution, the wave function in the transmitted region
appears as ![]() . If the transmitted region were
actually forbidden, then the solution there must behave like
. If the transmitted region were
actually forbidden, then the solution there must behave like
![]() . The only way for this to happen is if we make the
choice in sign,
. The only way for this to happen is if we make the
choice in sign,
This simple observation determines all of the rules for fundamental scattering
processes involving forbidden regions.
To determine the quantum amplitudes for a forbidden region, simply
use the corresponding amplitudes for the classically allowed case and
make the substitution (18). For instance, the quantum
amplitude for penetration through a region a (as opposed to
propagation) is then obtained as
![]() , consistent with our
previous result. Similarly, the reflection and transmission amplitudes
for crossing from an allowed region with wave vector k to a
forbidden region with decay constant
, consistent with our
previous result. Similarly, the reflection and transmission amplitudes
for crossing from an allowed region with wave vector k to a
forbidden region with decay constant ![]() , crossing from a
forbidden region with decay constant
, crossing from a
forbidden region with decay constant ![]() to an
allowed region with wave vector k, and crossing from a
forbidden region with decay constant
to an
allowed region with wave vector k, and crossing from a
forbidden region with decay constant ![]() to an other
forbidden region with decay constant
to an other
forbidden region with decay constant ![]() , are
, are
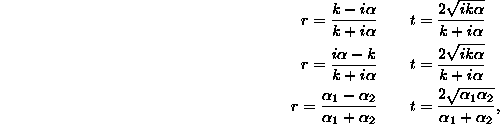
respectively.
The alternate way of determining the quantum amplitudes is to follow the procedure given in Section 3.5, solve the TISE explicitly for the case of interest and then to pick off the prefactors multiplying the unit wave functions when there is a unit incident beam. This procedure depends on the choice of unit wave functions. The choice which is consistent with the amplitudes of the previous paragraph is obtained by analytic continuation of the unit current classically allowed functions,
where ![]() and
and ![]() are the unit left- and right-
penetrating wave functions, respectively.
are the unit left- and right-
penetrating wave functions, respectively.